IDA NativeHook Analyzer ADD-ON
Custom Analysis Dashboard
Front-end Visualization and Encrypted Logic Restoration,
Focus on analysis, not complexity — Experience a simplified and access-restricted analysis environment.
Focus on analysis, not complexity — Experience a simplified and access-restricted analysis environment.
$199/year
- Flexible Licensing
- Easy Integration and Control
From
$399/year
From
$799/year

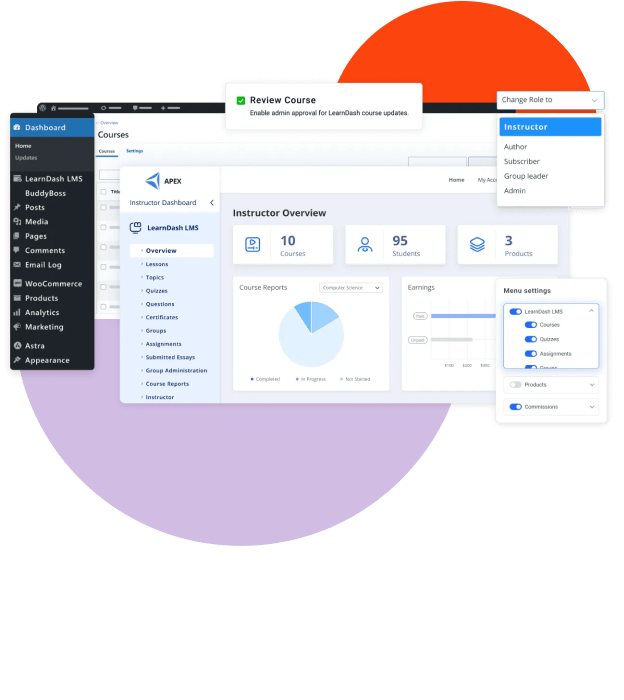
IDA NativeHook Analyzer Plugin
A native analysis toolkit tailored for IDA Pro plugin developers
Automatically detect entry points, reconstruct classes and vtables, and simplify Android SO reverse engineering and native hook research.
Deep IDA native-API integration
Seamlessly extend the official IDA API inside IDA with an interactive plugin UI.
Smart auto/manual renaming
Detect key entry points and symbols with manual correction and batch rename support.
String Xref & log clue tracing
Quickly locate UI text or log-related logic to aid analysis.
Easily reproduce and clean up function encryption logic with an interactive tracer
Smart entry-point detection
Automatically mark main logic entry points to reduce initial exploration time.
Vtable recovery & class ID
Auto-infer vtables and class relations with manual fine-tuning.
Encrypted logic tracing & cleanup
Provide step-trace tools and reusable cleanup script templates.
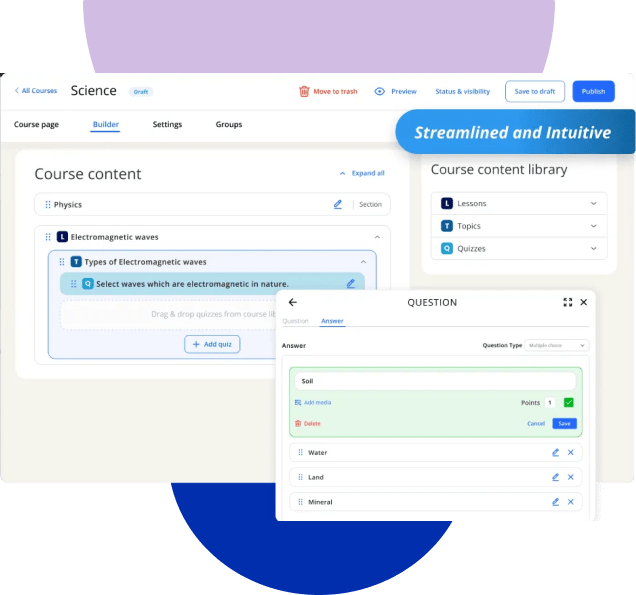
Fully customizable analysis dashboard and visualization
Modular analysis UI
Focused module views and call-relationship panels within IDA.
Interactive control-flow graph
Interactively inspect control flow, branches, and recovery paths.
Type reconstruction engine
Context-based type inference and auto-fix suggestions.
Intuitive class & vtable visualization
Show class inheritance, virtual function layout, and hook chains.
Powerful anti-debug bypass and hook utilities for reverse engineers
Anti-debug detection & bypass aids
Auto-annotate common anti-debug patterns and offer bypass hints.
OLLVM deobfuscation aids
Recognize OLLVM patterns and assist control-flow recovery.
Native hook workflow automation
Locate target functions and auto-generate hook/patch templates and scripts.
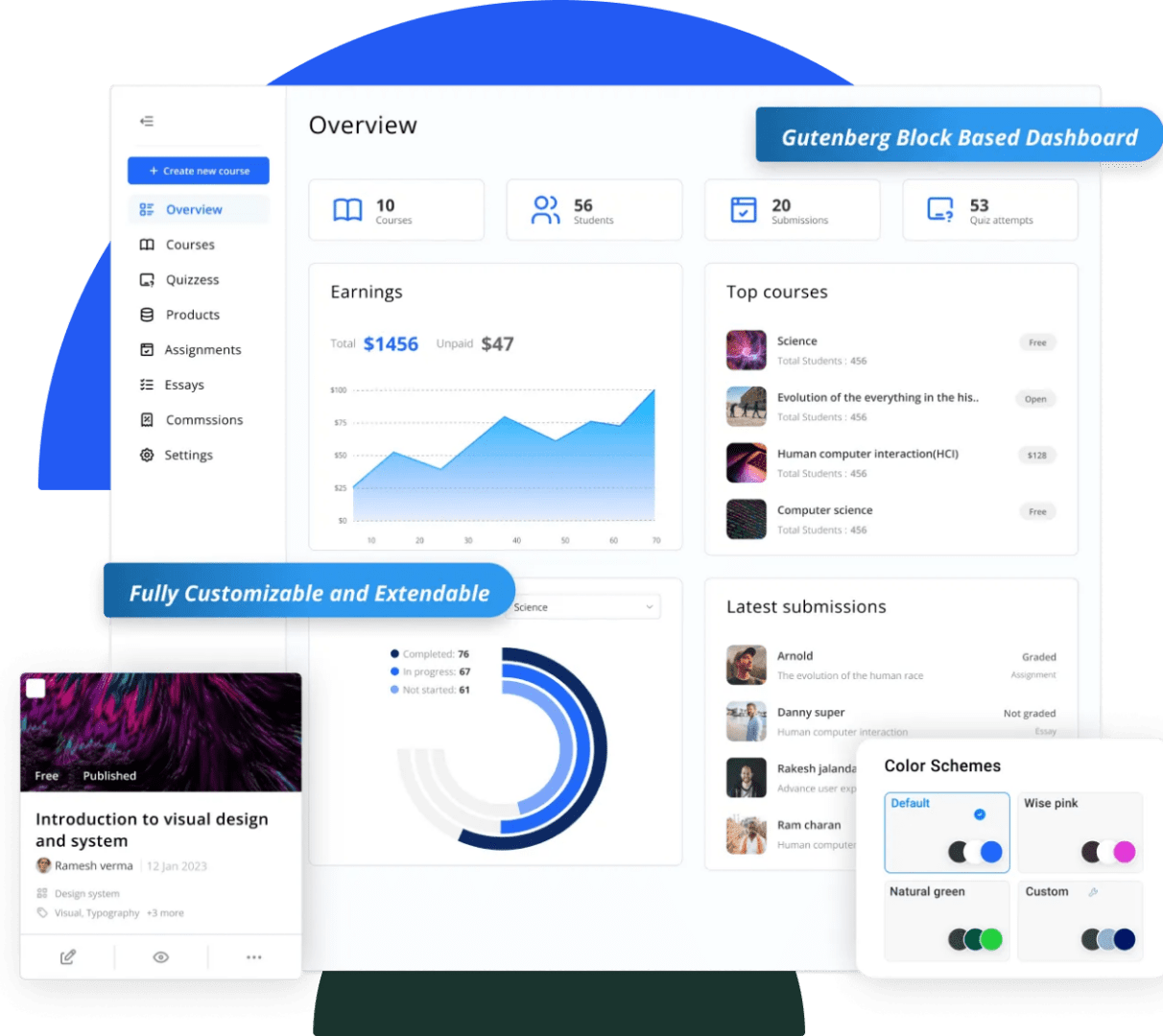
Comprehensive plugin-role and dashboard feature set
Plugin roles & permission control
Extend IDA with scoped permissions so the plugin acts only within required analysis bounds.
Backend analysis panel
Provides deep-analysis tools, logs, and a script execution console.
Frontend visual dashboard
Frontend-friendly views for interactive exploration without leaving IDA.
Frontend tracer & script-builder
Simplify function tracing, injection, and automation script creation.
Admin notifications & workflow control
Provide notifications and review triggers on key analysis events.
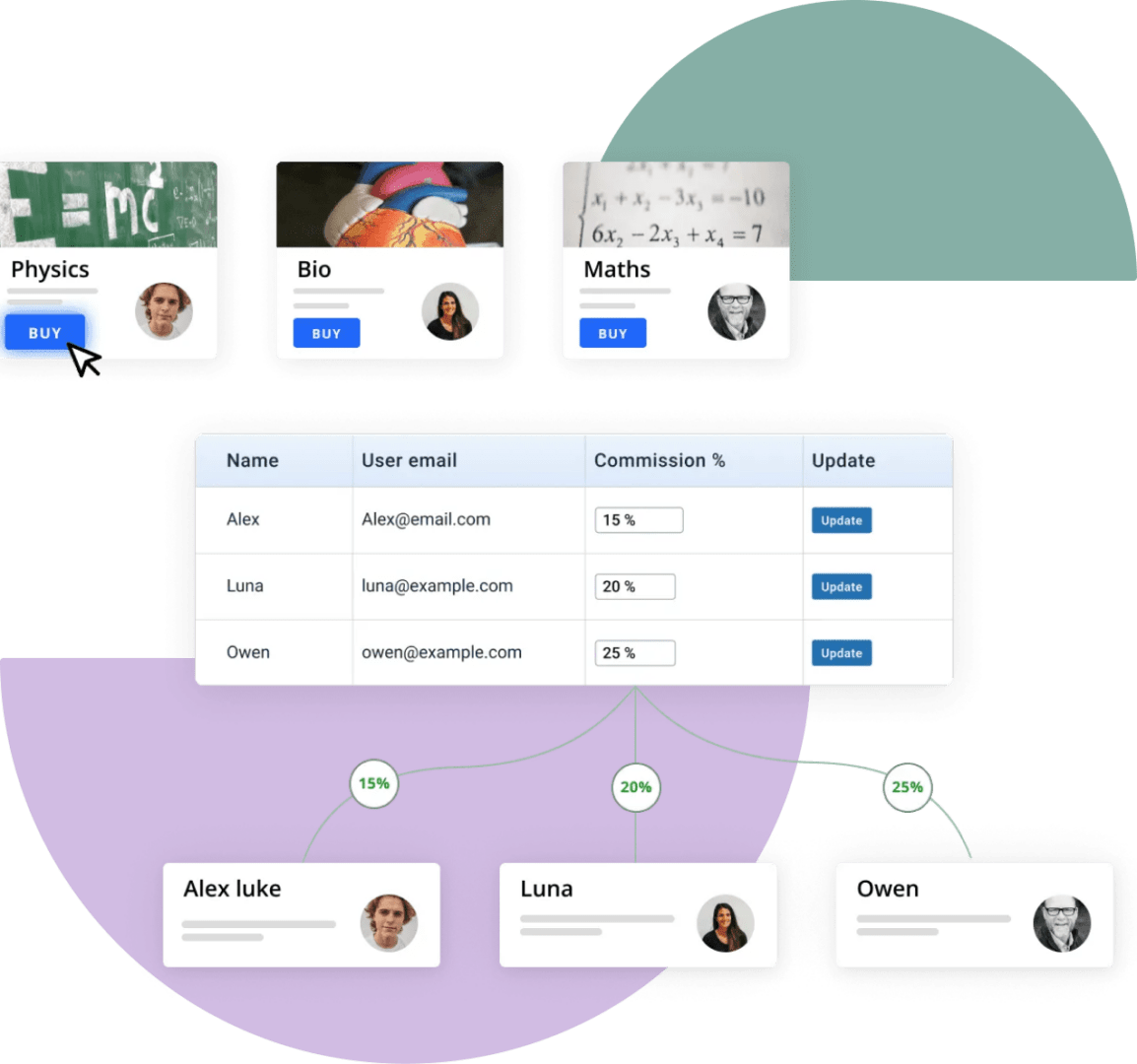
Collaborative analysis support
Support multi-user annotations and shared analysis templates.
Shared string & log view
Centralized view for string Xrefs and suspicious log clues.
Efficiency metrics & audit
Record analysis steps for reproducibility and performance assessment.
Extensible dev API
Expose Python/C++ extension points for secondary development and integrations.
FAQs
Feeling overwhelmed?

