
eBPF for System Behavior Analysis
Add-on
Advanced Kernel-Level Observability Course
Gain deep insights into system and app behavior through non-intrusive eBPF-based tracing. Learn to detect kernel-level SVC calls, monitor SSL/TLS network transmissions, and analyze app behaviors directly from the kernel layer without modifying source code.

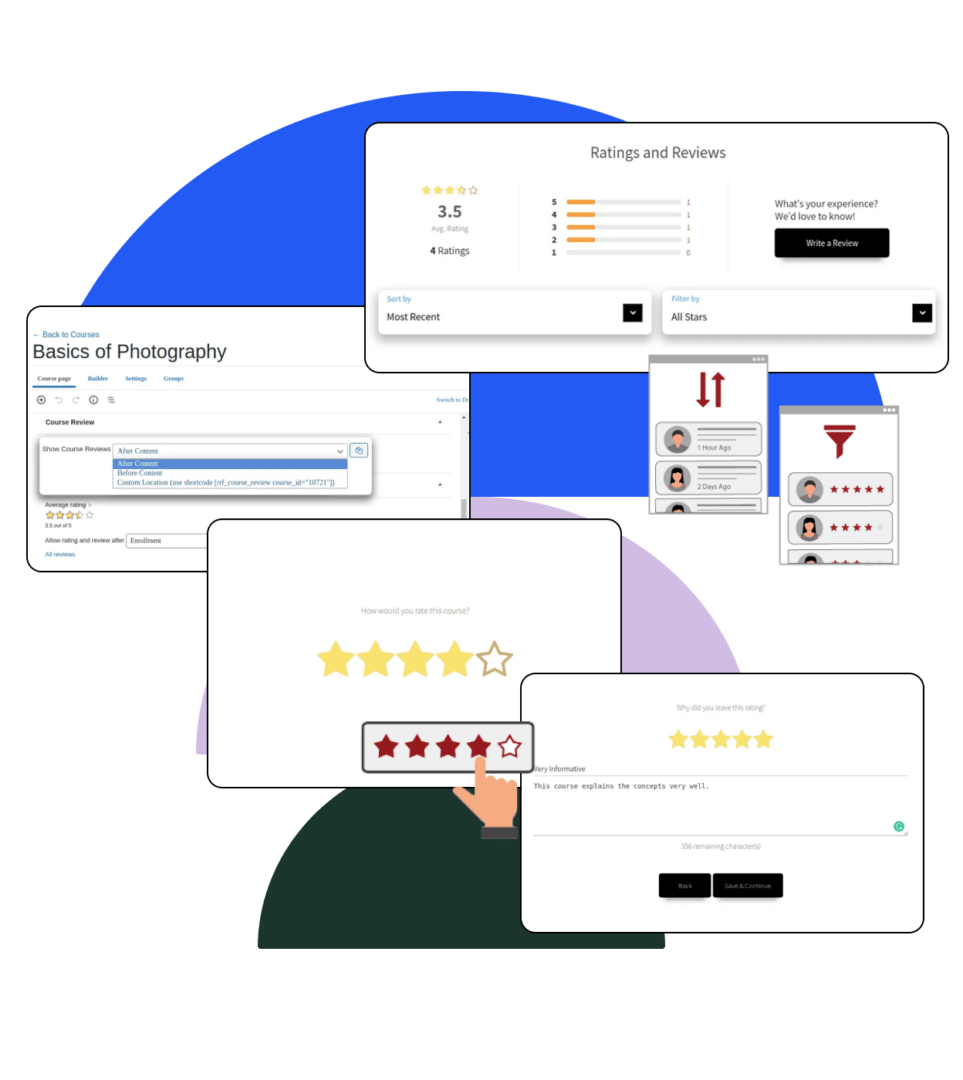
Understand and Monitor App Behavior at the Kernel Level
eBPF Fundamentals
Learn how eBPF (extended Berkeley Packet Filter) enables sandboxed code execution in the Linux kernel. You will gain full control over observability pipelines without modifying kernel source or application binaries.
Analyze System Calls (SVC and Syscalls)
Detect and trace Android’s low-level svc calls that connect user space and kernel space. Understand how to hook into syscall interfaces and monitor process behavior using kprobes, uprobes, and tracepoints.
Monitor Encrypted Network Data (SSL/TLS)
Leverage eBPF programs attached to socket-level events to trace SSL/TLS communications. Understand how to capture metadata such as IPs, certificates, and session information while respecting data privacy and encryption boundaries.
Non-Intrusive Behavior Analysis
Use eBPF to collect runtime data without modifying application code. This enables dynamic performance and security monitoring with zero overhead for end users.
Build Practical Skills
Kernel Data Structures and Probes
Master the key kernel components used in tracing — including BPF maps, perf events, and ring buffers. Learn how to attach probes to system and user functions in both native and Android environments.
Integration with Android
Understand how Android’s modified Linux kernel affects eBPF behavior. Learn how to deploy eBPF tools on rooted and non-rooted devices, integrate with libbpf, bpftool, and modern observability frameworks like bcc or libbpf-rs.
Real-World Examples
Tracing Binder IPC calls
Monitoring app network performance
Detecting abnormal SSL handshake patterns
Profiling CPU usage per process or thread
Debugging kernel-to-user interactions
Monitoring app network performance
Detecting abnormal SSL handshake patterns
Profiling CPU usage per process or thread
Debugging kernel-to-user interactions
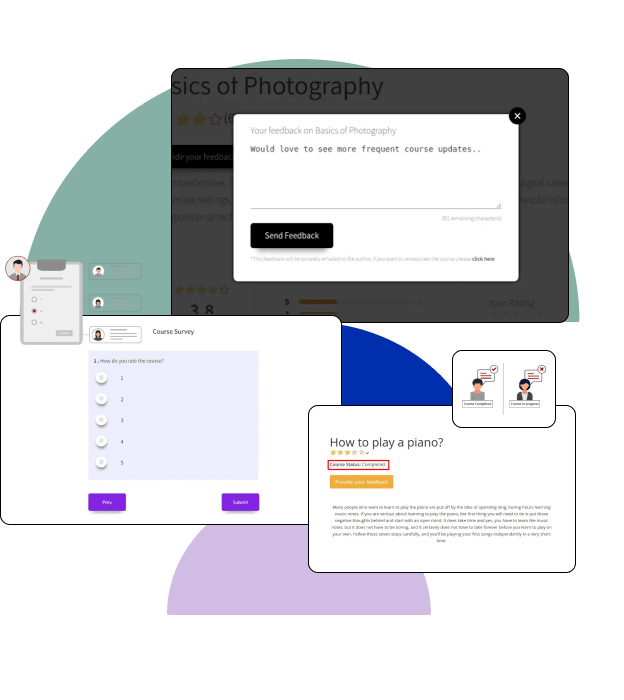
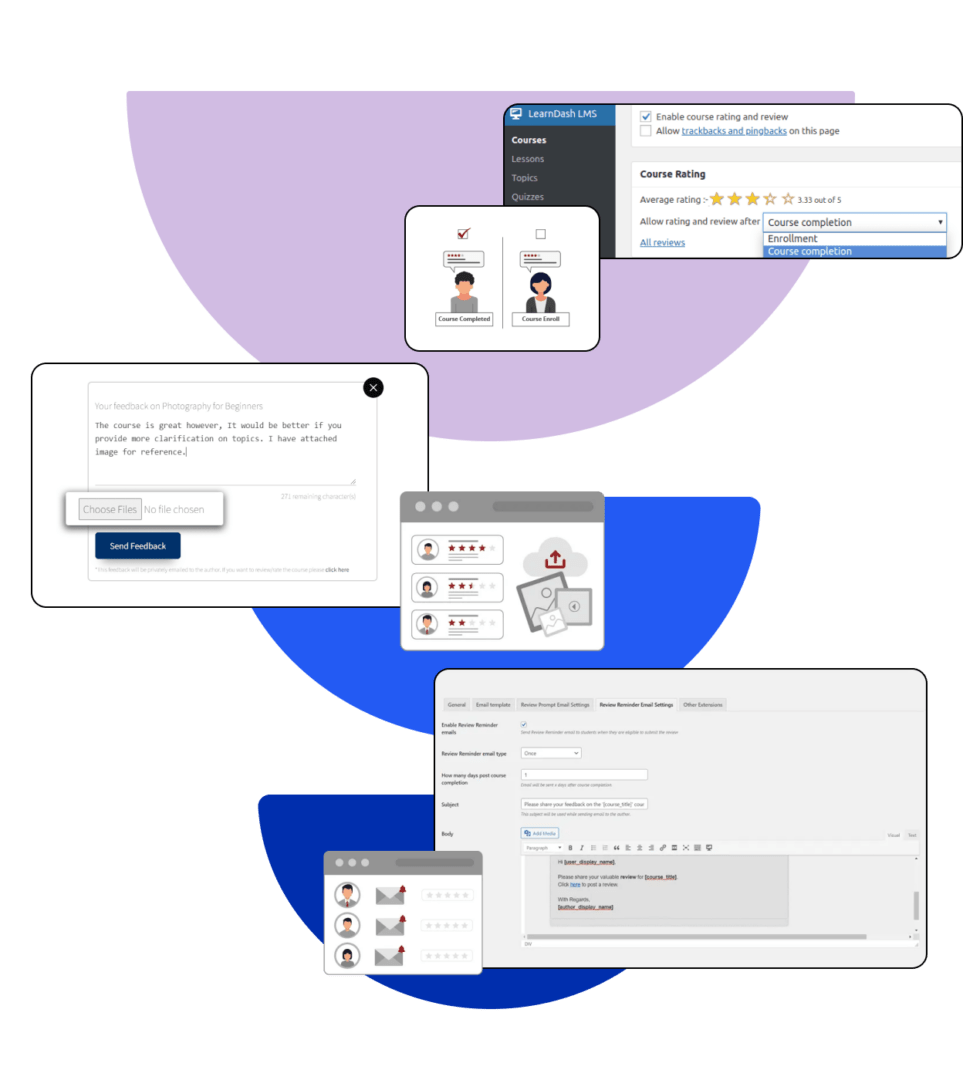
Feedback and Continuous Learning
Student Projects and Reports
Students will conduct hands-on kernel tracing experiments, build custom eBPF programs, and submit behavior analysis reports for review.
Automated Feedback System
Receive structured feedback on your eBPF tracing implementations, along with survey-based course evaluations to help improve your kernel analysis proficiency.
Certification
Students who complete all kernel tracing labs and submit a comprehensive Android analysis project will receive an official eBPF System Analysis Certificate.
What you get
Hands-on lab sessions demonstrating real eBPF programs. You will write and run kernel probes (kprobes, uprobes, tracepoints) to capture Android system events, syscall behaviors, and SSL/TLS transmission traces.
Use flexible configuration to trigger tracing only under defined conditions — for example, when specific apps, system calls, or sockets are active. Learn to manage eBPF lifecycle events and optimize performance with minimal kernel overhead.
Generate automated performance and security feedback reports after each lab. These reports summarize syscall frequency, latency, packet metadata, and app interaction metrics for deeper insight.
Set up kernel-level alert rules that automatically notify you when anomalous system behaviors occur — such as excessive SVC invocations, SSL handshake failures, or CPU spikes in a target process.
FAQs
Start mastering kernel-level tracing today.
